Some people like horror movies. I grew up with Frankenstein, the Werewolf, Dracula, and other vintage “monster movies.” I did not like them at all. Later in life “slasher movies” became even more popular. They were hacking people up with just about everything imaginable. Hacking people up, sold movie tickets. Just not to me.
The word “hacking” has been used to describe “cutting in a rough and violent way,” since around 1200 B.C. However its root, “hack”, has greatly expanded in the technology era. Let’s see how.
It all started back on June 1st, 1903, when a “wireless” Morse code message was meant to debut to a public audience in London. Guglielmo Marconi would later be awarded the Nobel Prize in Physics for this wireless technology, and later still, be credited for inventing the radio. The intention was to send the Morse code message, wirelessly, from London to Poldhu, in South Cornwall, England, 300 miles or 482 kilometers away.
A British inventor, magician, and perhaps the first technology hacker, Nevil Maskelyne, decided to “hack” the message. He built a 50-meter radio tower that would overpower the initial message.
Maskelyne replaced the public message with humorous limericks and insults. London’s newspapers did not use the term “hacked,” they used “scientific vandalism.”
Maskelyne stated that he hacked (paraphrased) the message to show how flawed the technology was, you know, for the common good.
In the early days of computing, hacking was more about curiosity and experimentation than malicious intent.
What was termed to be scientific vandalism 120 years ago, is at a whole different level today. Now, hackers are cybercriminals that illegally hack into systems with malicious intent. They find ways to exploit vulnerabilities with a virus or ransomware attacks. They are referred to as “black hat” hackers, the bad guys.
However, there are some hackers that hack systems to expose vulnerabilities. Like Maskelyne, for the greater good. Guess what they are referred to? You got it, the “white hat” hackers, the good guys. There is also a third type called “gray hat” hackers. They are not malicious but may not be considered totally ethical.
A few years ago, a couple of white hat hackers decided to test the vulnerability of a 2014 Jeep® that they had purchased new. Their intentions were good and planned to report on any possible security weakness. They were successful in taking control of the wipers, blasting the radio and even killing the engine. Further hacking proved the possibility of taking over the steering and the brakes!
An article came out about Jeep and their vulnerability which stunned the automotive manufacturers. Fiat Chrysler Automotive (FCA®) recalled 1.4 million vehicles for a security update!
Vehicles would need a secure gateway to protect them from hacking yet allow for diagnostic tool access. In automotive applications, a secure gateway is like a network firewall, protecting the internal vehicle network from external attack. External access to some functions requires authorization.
FCA® requires registration to access the vehicle through Security Link™.
Unlike FCA, Security Link on a Ford® is handled behind the scenes. An engineer would explain it in much greater detail, but we don’t really need to know how the clock works; we just want to know what time it is. I simply think of it like a secret code that we need to decipher to unlock the door to the Ford computer. Security Link is like a decoder ring that deciphers that code.
Security from hackers is obviously an important issue, and Security Link access is required even on simple repairs. Let’s look at a case study that shows a great example of that.
2018 Ford Focus® – Replaced the battery. Now a scan tool is required to reset the battery monitor system (BMS)

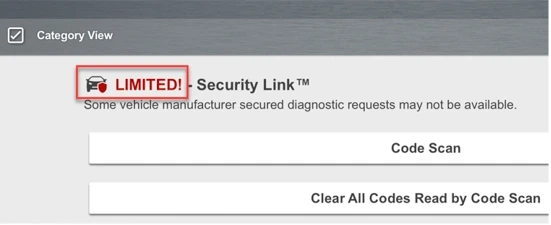
When I plug in my scan tool and get the message below, I cannot get into service resets and relearns, to complete this job. Two things are needed for Security Link to get us past Fords security. The third item, Profile Manager Account, is optional but highly recommended to stay abreast of any changes with OEMs concerning Security Link.
1. Scanner connected to Wi-FI
2. Current software in scanner
3. Snap-on Profile Manager account. To create a Profile Manager account, go to profilemanager.mitchell1.com Optional – highly recommended.
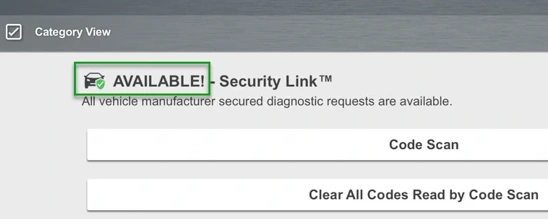
Once those three criteria have been met, you will be granted full access shown below.
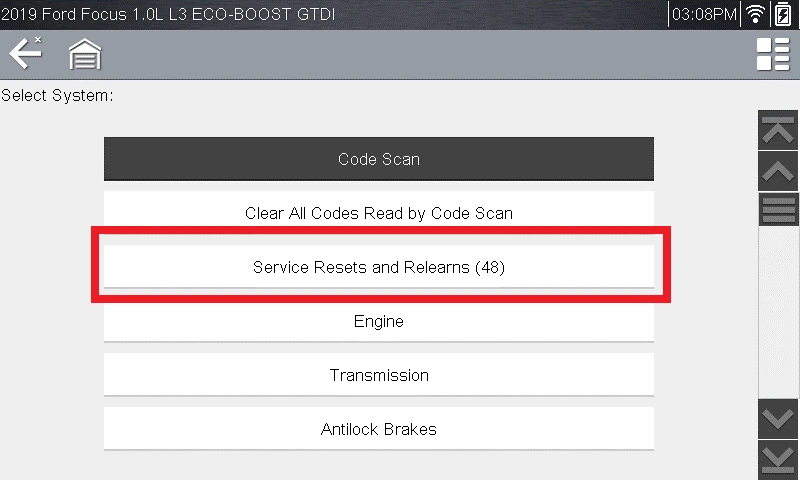
After vehicle ID we will need to go to Service Resets and Relearns.
Battery Monitor System reset is found under Replace Battery, then Functional Tests and Calibrations.
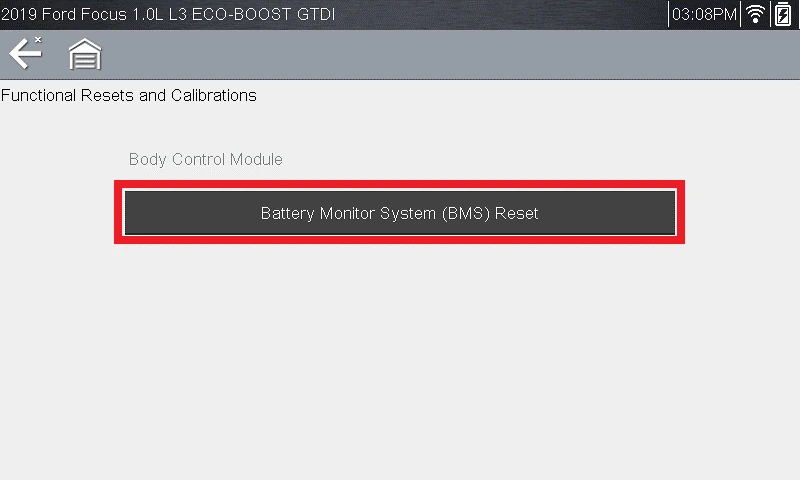
The diagnostic request requires a Security Link session.
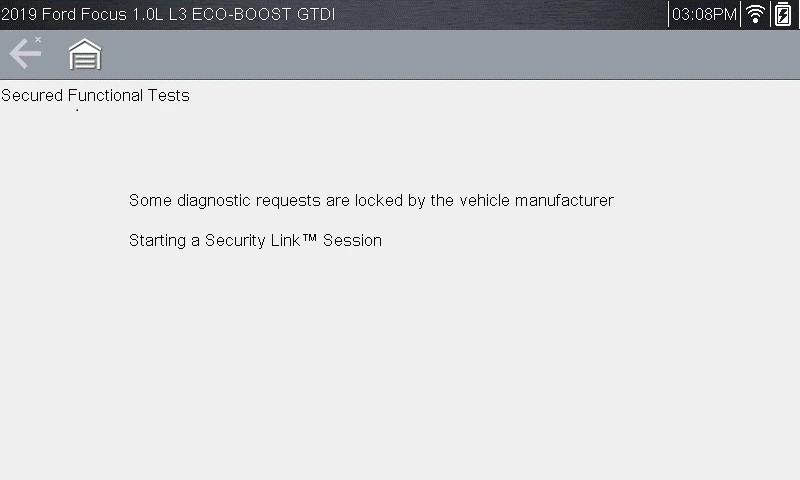
The scan tool will prompt you that the reset is complete.
Here is a special question for shop owners. When writing an estimate to replace a battery, do you take into consideration an added charge for scanner use to reset the BMS?
I hope this article helps with understanding that Security Link really prevents the task of diagnosing today’s vehicles from becoming a horror movie. By the way, I love western movies, and I always root for the good guys in white hats.
